Psiphon Team
5/9/2016
In December, Psiphon blogged about a previous blocking event in Brazil, available here.
Psiphon use surged again in Brazil in response to another nationwide suspension of WhatsApp messaging service. On May 2nd, Brazilian state judge Marcel Maia Montalvão issued an order to block WhatsApp for 72 hours. The judge is seeking user data from WhatsApp as part of a criminal investigation. The five main mobile operators were ordered to block the messaging service, beginning at Monday at 2 p.m. local time.
In response to the recent suspension of WhatsApp services, company CEO Jan Koum posted a message to Facebook stating, “Yet again millions of innocent Brazilians are being punished because a court wants WhatsApp to turn over information we repeatedly said we don’t have. Not only do we encrypt messages end-to-end on WhatsApp to keep people’s information safe and secure, we also don't keep your chat history on our servers. When you send an end-to-end encrypted message, no one else can read it – not even us.”
The suspension was overturned by another judge on Tuesday following an appeal from WhatsApp’s lawyers, allowing WhatsApp to resume services in Brazil.
In March, Judge Montalvão ordered the arrest of Facebook executive Diego Dzodan on charges of obstructing justice after WhatsApp failed to deliver messages subpoenaed in the criminal investigation. A day later, an appeals judge overturned that order and Dzodan was released. Although WhatsApp is owned by Facebook Inc, the two companies operate separately.
During a press conference that followed, Dzodan stated that WhatsApp is unable to turn over the data because it doesn’t store users’ messages after they’ve been delivered. In addition, the messaging service uses end-to-end encryption and messages cannot be intercepted.
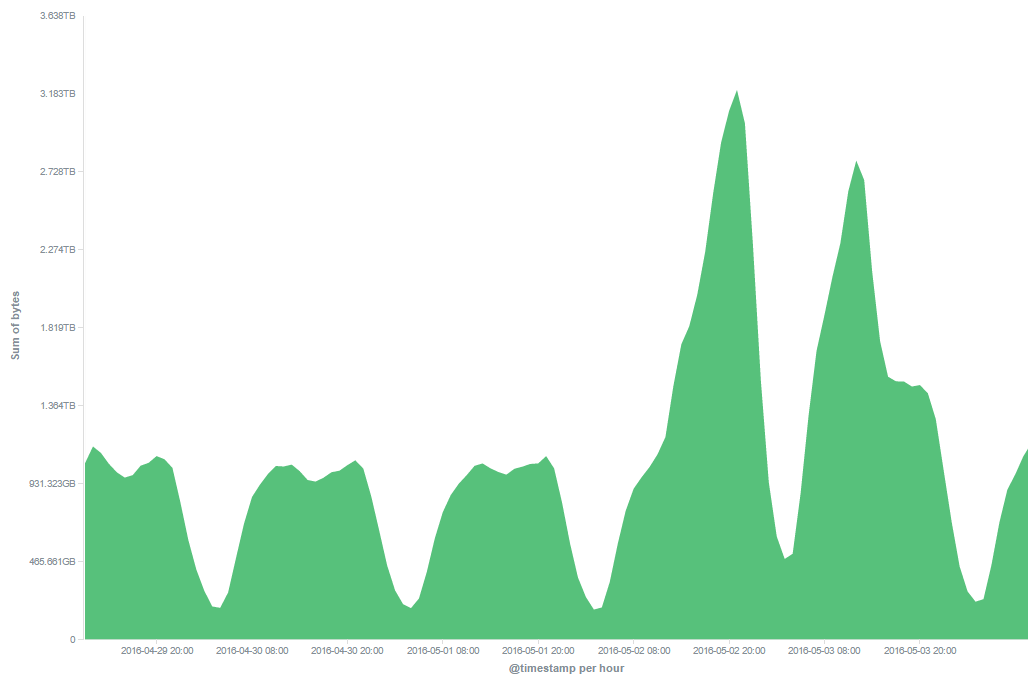
Using Psiphon, Brazil’s WhatsApp users were able to retain or restore access to the application. The Psiphon user base in Brazil tripled within the first 24h of the ban. Brazil’s Globonews network recommended Psiphon to circumvent the blocking.
Psiphon in Brazil: bytes per hour, 29 April – 4 May 2016
This case demonstrates that in response to censorship, blocking, and other restrictions, internet users will turn to known tools that connect them to content and to each other.






 Psiphon helped maximize the global impact of the campaign, connecting the festival’s LGBT filmmakers and their stories to audiences in 135 countries around the world, in some of the most heavily censored societies — places where freedom of expression is not a given, in particular for members of the LGBT community. According to #FiveFilms4Freedom Director Alan Gemmell, the initiative “was a truly ground-breaking way to support freedom and equality all over the world and showcase some of our finest short filmmakers… we’re incredibly proud that our campaign reached tens of millions of people and that we were able to show solidarity with people around the world who risk their lives everyday just to live and love.”
Psiphon helped maximize the global impact of the campaign, connecting the festival’s LGBT filmmakers and their stories to audiences in 135 countries around the world, in some of the most heavily censored societies — places where freedom of expression is not a given, in particular for members of the LGBT community. According to #FiveFilms4Freedom Director Alan Gemmell, the initiative “was a truly ground-breaking way to support freedom and equality all over the world and showcase some of our finest short filmmakers… we’re incredibly proud that our campaign reached tens of millions of people and that we were able to show solidarity with people around the world who risk their lives everyday just to live and love.”